
Ten malicious packages mimicking official software program initiatives within the npm registry obtain an information-stealing element that collects delicate information from Home windows, Linux, and macOS techniques.
The packages have been uploaded to npm on July 4, and remained undetected for a protracted interval as a result of a number of layers of obfuscation that helped escape commonplace static evaluation mechanisms.
In accordance with researchers at cybersecurity firm Socket, the ten packages counted almost 10,000 downloads and stole credentials from system keyrings, browsers, and authentication companies.
On the time of writing, the packages are nonetheless obtainable, regardless of Socket reporting them to npm:
- typescriptjs
- deezcord.js
- dizcordjs
- dezcord.js
- etherdjs
- ethesjs
- ethetsjs
- nodemonjs
- react-router-dom.js
- zustand.js
Socket researchers say that the packages use a faux CAPTCHA problem to seem official and obtain a 24MB infostealer packaged with PyInstaller.
To lure customers, the risk actor used typosquatting, a tactic that leverages misspellings or variations of the official names for TypeScript (typed superset of JavaScript), discord.js (Discord bot library), ethers.js (Ethereum JS library), nodemon (auto-restarts Node apps), react-router-dom (React browser router), and zustand (minimal React state supervisor).
When looking for the official packages on the npm platform, builders might mistype the identify of the official package deal or choose a malicious one listed within the outcomes.
Upon set up, a ‘postinstall’ script is triggered robotically to spawn a brand new terminal that matches the host’s detected OS. The script executes ‘app.js’ exterior the seen set up log and clears the window instantly to evade detection.
The ‘app.js’ file is the malware loader which employs 4 obfuscation layers: self-decoding eval wrapper, XOR decryption with dynamically generated key, URL-encoded payload, and heavy control-flow obfuscation.
The script shows a faux CAPTCHA within the terminal utilizing ASCII to offer false legitimacy to the set up course of.
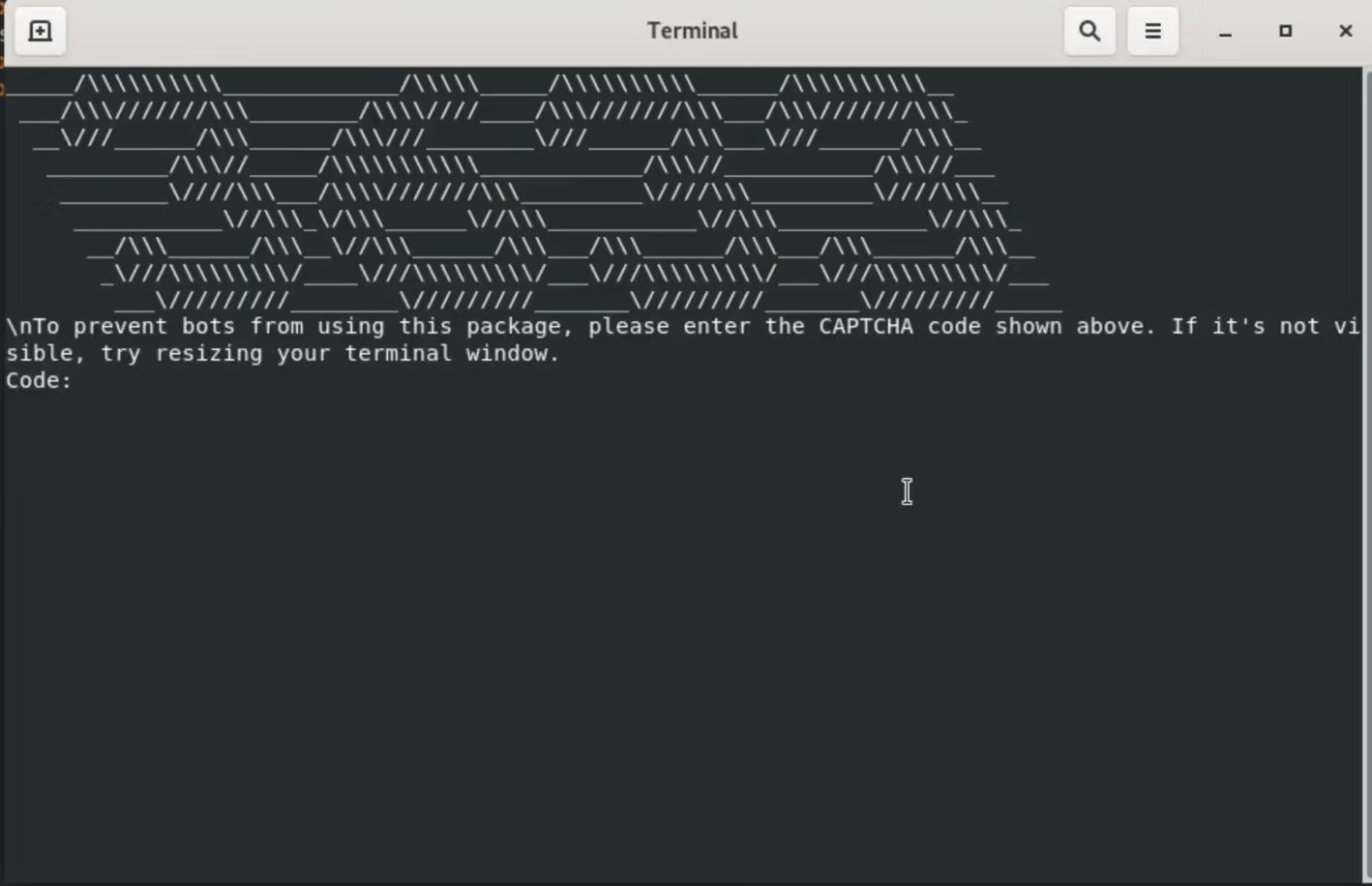
Supply: Socket
Subsequent, it sends the sufferer’s geolocation and system fingerprint info to the attacker’s command and management (C2) server. Having acquired this info, the malware downloads and robotically launches a platform-specific binary from an exterior supply, which is a 24 MB PyInstaller-packaged executable.
The data stealer targets system keyrings akin to Home windows Credential Supervisor, macOS Keychain, Linux SecretService, libsecret, and KWallet, in addition to information saved in Chromium-based and Firefox browsers, together with profiles, saved passwords, and session cookies.
Furthermore, it seeks SSH keys in widespread directories, and likewise makes an attempt to find and steal OAuth, JWT, and different API tokens.
The stolen info is packaged into compressed archives and exfiltrated to the attacker’s server at 195[.]133[.]79[.]43, following a brief staging step in /var/tmp or /usr/tmp.
Builders who downloaded any of the listed packages are really helpful to scrub up the an infection and rotate all entry tokens and passwords, as there’s a good probability that they’re compromised.
When sourcing packages from npm or different open-source indexes, it’s advisable to double-check for typos and be sure that every little thing comes from respected publishers and official repositories.


