Abstract created by Sensible Solutions AI
In abstract:
- Macworld explains the right way to determine in case your Mac has been compromised, overlaying key warning indicators like overheating, browser hijacks, unknown apps, and extreme CPU utilization in Exercise Monitor.
- Mac customers want this information since Macs will be hacked by way of malware, spyware and adware, ransomware, and port exploits, regardless of widespread beliefs about their immunity.
- Important steps embody disconnecting Wi-Fi, checking system settings for suspicious accounts, working antivirus scans, and updating macOS instantly. Detailed directions are offered under.
It’s a long-held perception of Mac customers that their computer systems are proof against the form of malware and viruses that plague Home windows PCs. Whereas there’s some credibility on this concept, we shouldn’t get over-confident with regards to Mac safety, as there are exploits that criminals can use to hack your Mac and go away it like a wide-open door by way of which they will steal your information or worse.
On this article, we check out whether or not Macs will be hacked, the right way to inform in case your Mac has been hacked or if somebody is spying in your Mac, and what you are able to do in case your Mac is being remotely accessed. Right here’s what you have to know – and what you have to do.
Indicators your Mac has been hacked: At a look symptom guidelines
First some reassurance: you most likely haven’t been hacked. It’s extra probably that you’re coping with buggy macOS conduct or app associated issues. Sadly generally a macOS replace could cause your Mac to start out behaving in an odd means, Highlight indexing, or a kernal-task associated to temperature management could cause excessive CPU utilization, as we have now discovered on many events.
However generally the behaviour actually is suspicious. The issues to look out for embody:
- Mac working actually scorching, very gradual, and the followers very loud when idle.
- Browser-based hijacks, a change to your standard House Web page, redirects, extensions you didn’t set up, and suspicious pop-ups – particularly if they are saying ‘Your Mac is contaminated’.
- Apps you didn’t set up, or don’t bear in mind putting in.
- Extreme use of CPU in Exercise Monitor.
If not one of the above apply, your Mac is unlikely to have been hacked. In case you are nonetheless involved, learn on for particulars of the right way to run the checks to substantiate whether or not your Mac has been hacked.
PROMOTION
Defend Your Mac: Intego Mac Premium Bundle
Intego Mac Web Safety X9 presents a helpful set of safety utilities that assist preserve your Mac protected and working easily and its user-friendly interface is true at house with Apple’s macOS aesthetic. It’s Macworld’s Editors Selection.
Now $29.99 (down from $84.99) for the primary 12 months.
What to do in case your Mac has been hacked
In case you are satisfied you’ve been hacked, then we suggest you do the next:
- Disconnect Wi-Fi.
- Change vital passwords utilizing a distinct machine – together with your Apple ID.
- Search for any unknown gadgets related together with your Apple ID and take away any which can be suspicious.
- Test for unknown admin accounts, login gadgets, distant entry settings, and configuration profiles (we provide particulars on how to do that under).
- Backup your information rigorously (you don’t need your backup to be contaminated with malware).
- Run a Mac antivirus.
- Replace macOS if there are any macOS updates that must be utilized.
- Run a clear set up of macOS in case you are certain you have been compromised.
- Allow FileVault and Firewall in your Mac if it’s not already turned on.

Dominik Tomaszewski / Foundry
Learn how to inform if Mac is hacked
In the event you suppose your Mac has been hacked there are a couple of methods to search out out. First, search for the indicators: Has your Mac slowed down? Is your internet connection painfully gradual? Do the adverts you’re seeing look a bit extra dodgy than standard? Have you ever observed something unusual in your financial institution statements?
In the event you concern your Mac might have been hacked, listed here are some fast issues you are able to do to verify for indicators your Mac has been compromised:
Test System Settings
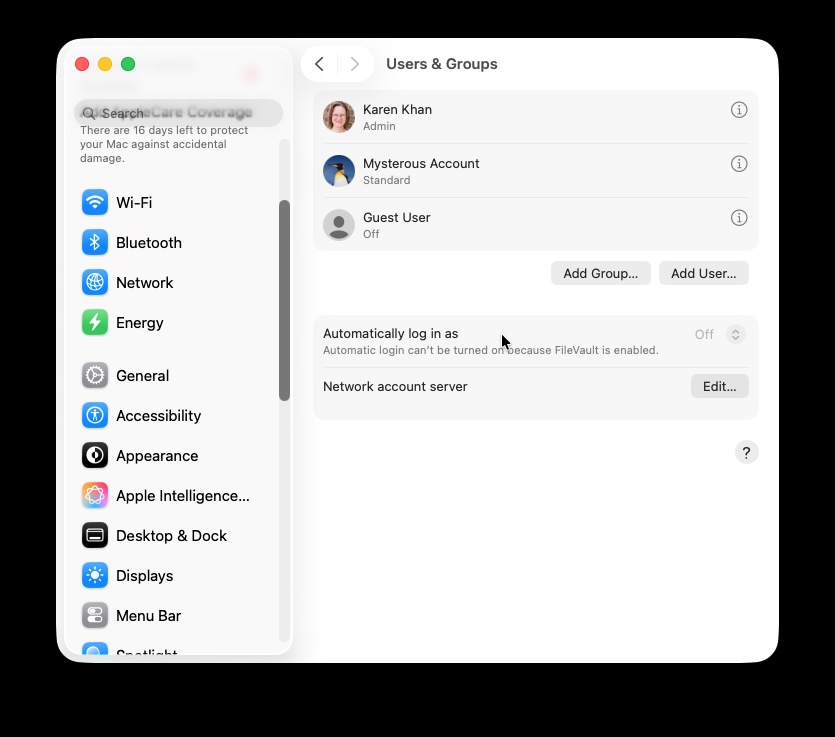
Test to see if a brand new admin account has appeared.
Foundry
In System Settings you’ll be able to search for indicators that your Mac has been accessed by somebody aside from your self.
- Open System Settings.
- Go to Customers & Teams to see if a brand new admin account has been added.
- Be certain that your personal account sort hasn’t modified.
- Search for unknown login merchandise in System Settings > Normal > Login Objects & Extensions. Are there any apps set to launch at startup that you just didn’t set up?
- Are there any suspicious apps which have been given permission for App Background Exercise that you just have been unaware of?
- Test for any extensions you don’t bear in mind putting in within the Extension part.
- Go to System Settings > Privateness & Safety and verify Distant Desktop to see if any purposes have requested entry. Look our for sudden display screen sharing or distant entry enabled. Test your distant entry settings.
- In Privateness & Safety verify to see if something has been granted Full Disk Entry.
- Additionally in Privateness & Safety verify for any Profiles that you just didn’t set up (you might not see something, which is nothing to fret about).
- Go to System Settings > Normal > Sharing and verify Display screen Sharing, Distant Login, Distant Administration and File Sharing to see if they’ve been enabled with out your information.
Test Exercise Monitor
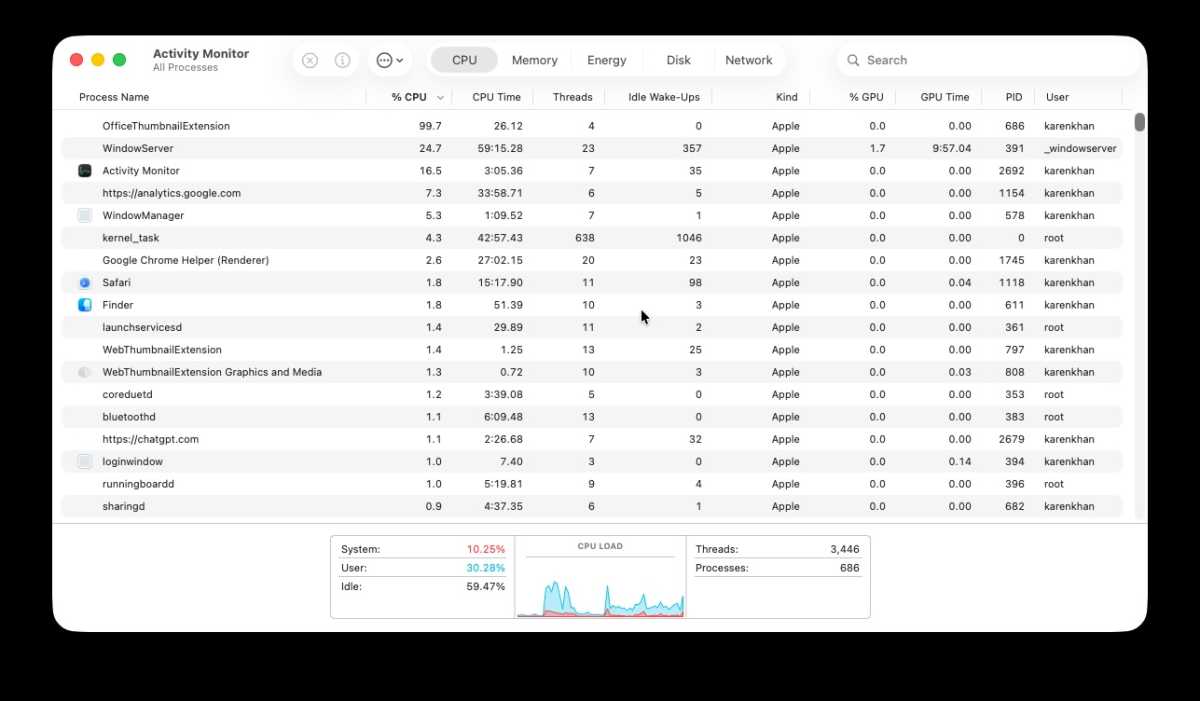
We checked: OfficeThumbnailExtension pertains to QuickLook on the Mac and doesn’t appear to be malicious, simply annoying!
Foundry
Exercise monitor is an effective way to verify for errant processes which can be working in your Mac. One among these processes could also be what’s inflicting the signs which have made you involved about your Mac, though it doesn’t essentially imply you’ve been compromised.
- To verify for suspicious processes working in your Mac open Exercise Monitor.
- Click on on View > All Processes.
- Click on on the CPU tab.
- Kind by % CPU.
- Be aware any apps or processes utilizing greater than 50% of your CPU whereas your Mac is idle. Excessive CPUs are usually related to browsers, video apps and video games, anything can be uncommon.
- Search for any apps or processes you don’t recognise
- In the event you see one thing that appears suspicious Google the method identify (however it’s most likely nothing to fret about and could also be very important on your Mac).
- Subsequent, click on on the Community tab.
- Kind by despatched bytes.
- Be aware something that’s sending massive quantities of information if you find yourself not importing something. Be suspicious of something sending massive quantities of information out, however Google unknown course of names earlier than deleting/quitting any processes.
- Now verify Reminiscence utilization in Exercise Monitor by clicking on the Reminiscence tab.
- Look out for apps consuming a number of RAM.
- Search for proof of distant entry, e.g. processes like: screensharingd, ARDAgent, sshd, isolated, and instruments like TeamViewer.
Search for suspicious apps
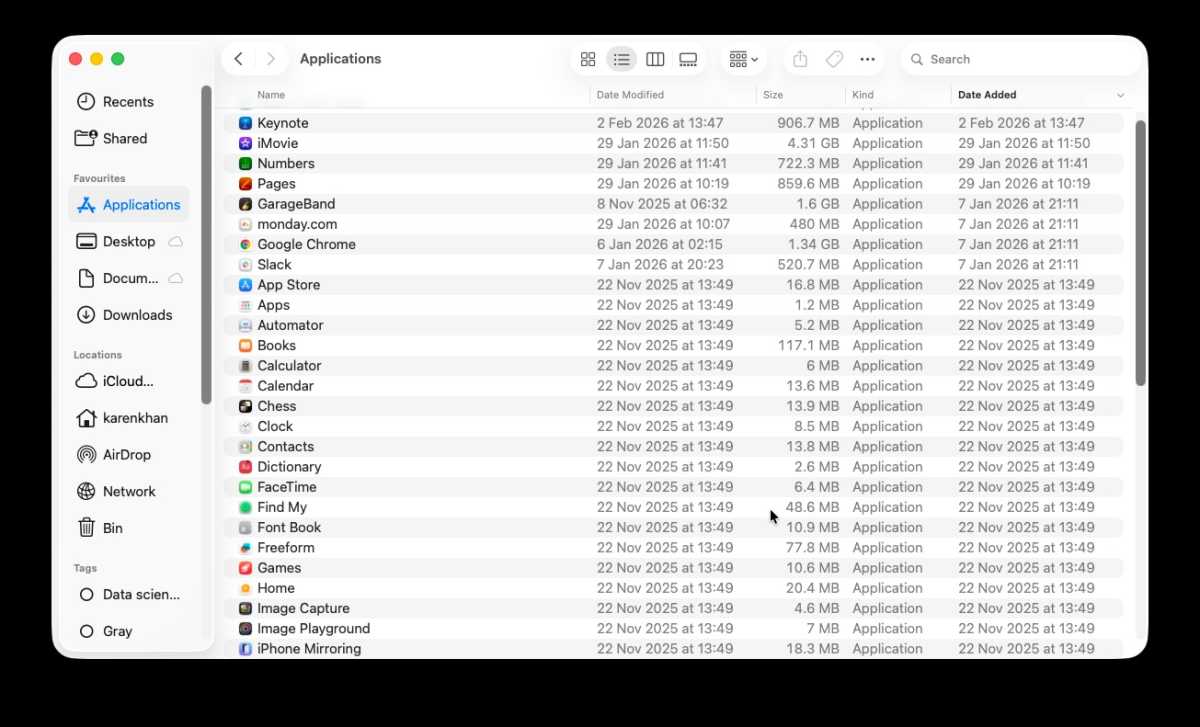
Nothing suspicious wanting, however watch out for duplicate apps that could possibly be spoofs.
Foundry
Take a look for any apps you don’t bear in mind putting in.
- Open the Finder.
- Go to the Functions folder.
- Kind by Date Added (if this isn’t an possibility proper click on on the bar and select Date Added).
- Search for any apps you don’t recognise or don’t bear in mind putting in.
Test Browser Extensions
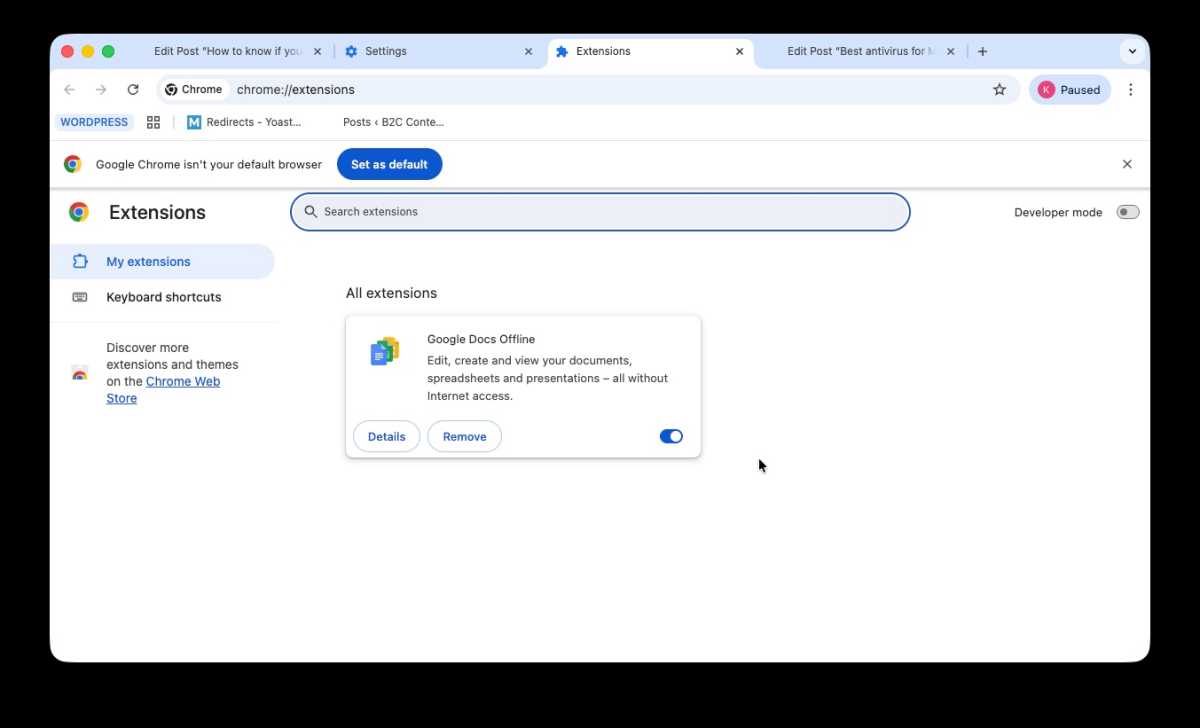
Test Chrome and Safari to see if there are any Extensions you don’t bear in mind putting in.
Foundry
Browser hijacks are doable even when your complete system isn’t hacked, so you’ll want to verify Safari, Chrome, FireFox and some other browser you utilize.
- Search for extensions you don’t bear in mind putting in, and delete them.
- In Safari click on on Safari > Extensions.
- In Crome click on on Chrome > Settings > Extensions.
Scan your Mac with an antivirus answer
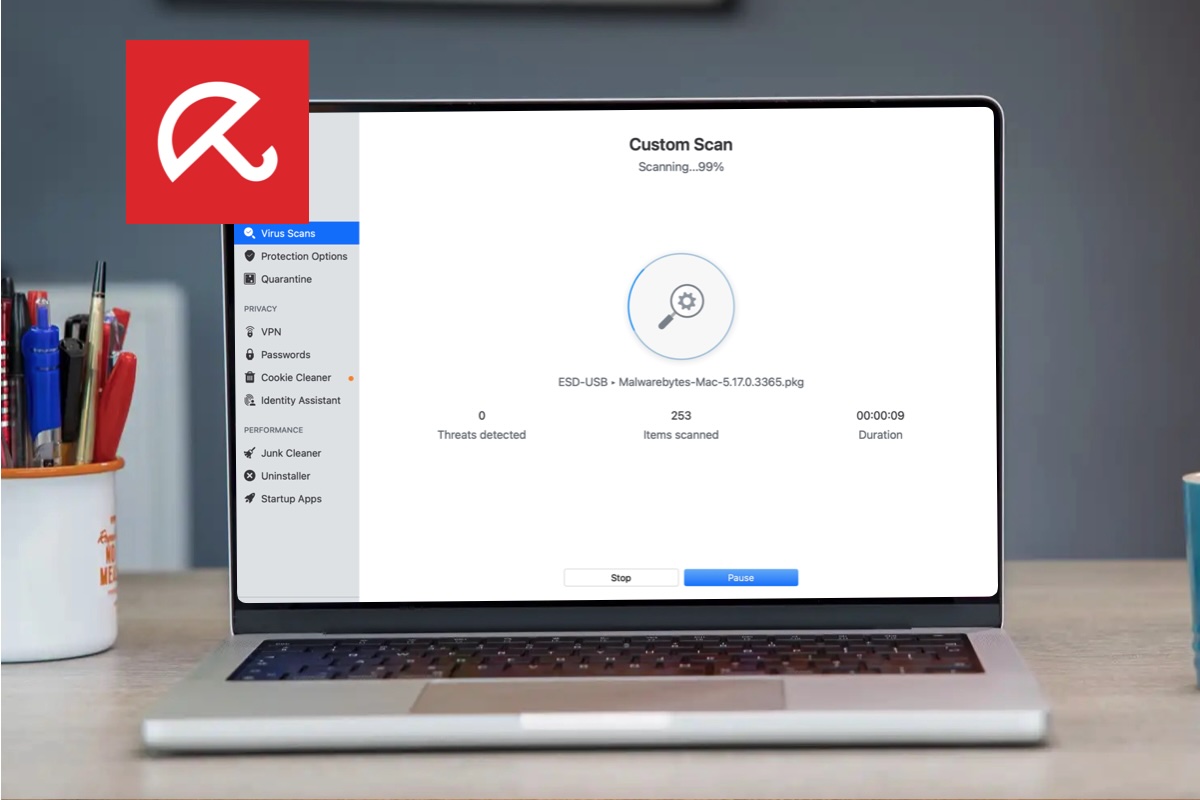
Run a Mac Antivirus answer and scan to see if there’s any malware in your Mac.
Foundry
macOS will routinely scan your Mac for any malware definitions that options in XProtect, however you’ll be able to’t drive it to do that. Due to this fact we strongly suggest that you run a Mac virus scan utilizing a 3rd celebration safety app.
Initiating a virus scan is a simple course of that often begins with the person clicking a Scan or Sensible Scan button.
There are numerous Mac Antivirus apps we suggest, our best choice for Mac customers being Intego, however there are many choices, together with some free Antivirus apps. See: Finest Mac Antivirus software program for one of the best choices.
You may additionally prefer to learn our information on the right way to take away a virus from a Mac.
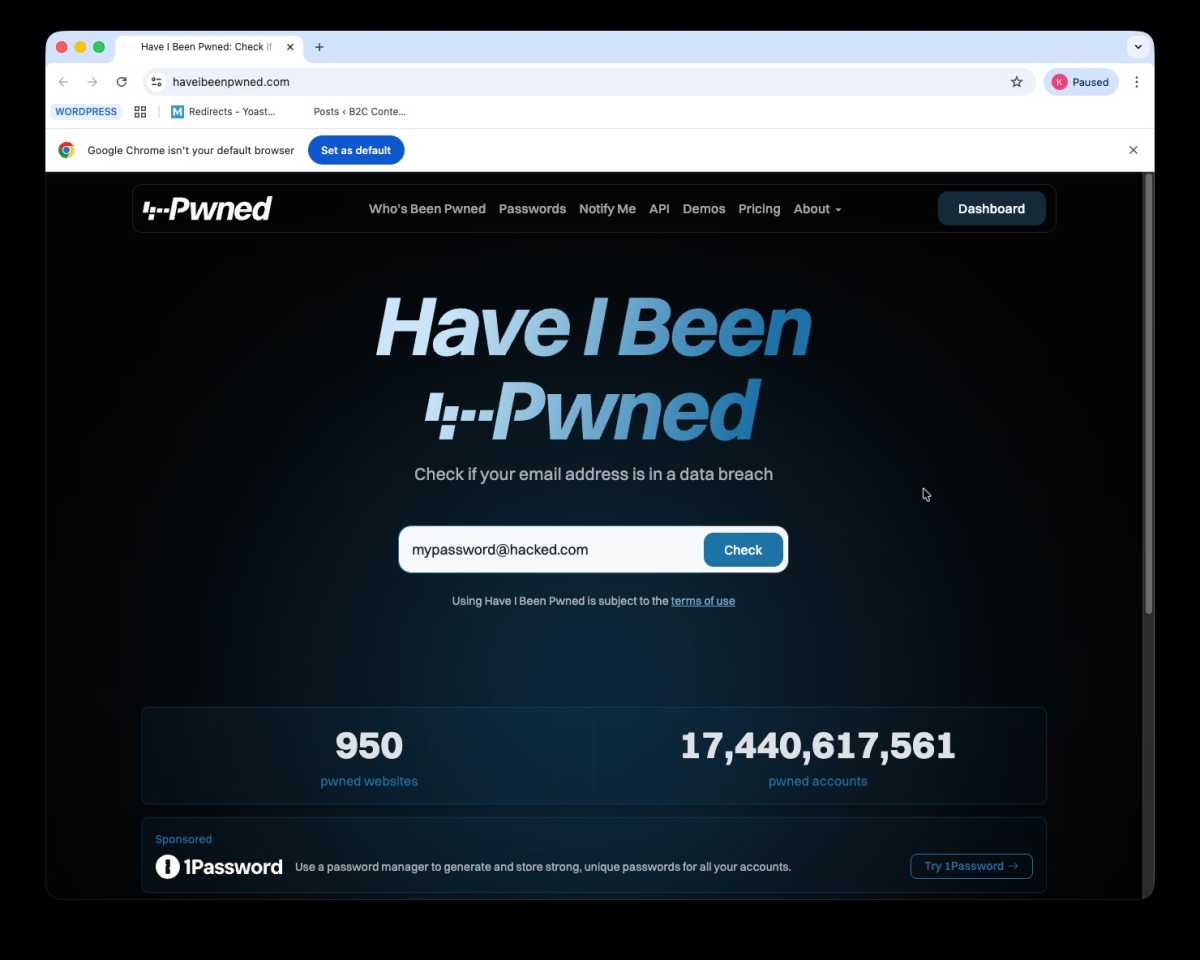
Test your password
Screenshot
Foundry
In the event you suppose an account may need been hacked then verify the web site haveibeenpwned.com and pop in your e mail handle to see if it’s featured in a knowledge breach. If it has been then change your password! This doesn’t imply you’ve been hacked, however it’s actually doable that if this info is on the market you might be.
Learn how to defend your Mac from hackers
macOS is a really safe system, so there’s no have to panic, however if you wish to cut back the possibilities of being compromised then there are some things to do.
- The primary is to solely obtain software program from both the Mac App Retailer or the official web sites of producers.
- You must also keep away from clicking on hyperlinks in emails in case they lead you to spoof web sites and malware.
- Don’t use USB cables, different cables, or reminiscence sticks, that if you happen to can’t ensure that they’re protected.
- If you end up searching the net surf in non-public or incognito mode.
- In the event you ever obtain a ransomware request or a phishing e mail don’t reply as all this does is verify that you just exist.
- One other is to ensure you obtain updates to macOS as quickly as they develop into obtainable as they often embody safety patches. In actual fact, you’ll be able to arrange your Mac to routinely obtain such updates. Activate Automated Updates in System Settings > Software program Replace, click on on the i beside Automated Updates and choose all of the choices. Pre-Ventura, go to System Preferences > Software program Replace and click on beside Routinely preserve my Mac updated pre-Ventura.
- Lastly, think about using a devoted safety software program bundle. You’ll discover our decide of the present choices in greatest Mac antivirus. Proper now our prime selections are Intego Mac Web Safety, however we additionally like McAfee Whole Safety, and Norton 360 Deluxe.
- You must also think about using a password supervisor, as this can will let you have a number of, difficult login particulars throughout all of your accounts with out having to recollect them. Right here our suggestions are LastPass, 1Password, and NordPass.

Dominik Tomaszewski / Foundry
FAQ
Can Macs get hacked?
It might be uncommon when in comparison with Home windows, however sure, there have been circumstances the place Macs have been accessed by hackers.
These sorts of assault aren’t prone to have an effect on most people although, so if you happen to aren’t defending state secrets and techniques or closely invested in cryptocurrency you’re unlikely to fall fowl of such an assault.
What are some examples of Macs being hacked
There are numerous forms of Mac malware which have been found ‘within the wild’ on Macs as you’ll be able to see from our run-through of the varied threats affecting macOS: Listing of Mac viruses, malware and safety flaws.
Quickly after launch, Malware focused the M1 Mac – examine Silver Sparrow and the first circumstances of malware for M1 Macs.
In August 2023 a software program developer launched particulars a few flaw in App Administration, a safety characteristic launched in macOS Ventura designed to forestall malicious software program modifications and alerting the person in such an occasion. The developer had found the difficulty earlier than the discharge of Ventura in October 2022, however a repair was not instantly issued, so, in August 2023, the developer went public with particulars of the flaw which meant that apps might bypass the verify by App Administration. Extra right here.
In December 2023, a gaggle of college researchers alerted Apple to a vulnerability in Apple’s M-series chips that may be exploited to realize entry to cryptographic keys. Dubbed “GoFetch,” the vulnerability could possibly be utilized by an attacker to entry a person’s encrypted information.
In April 2024 Apple alerted some customers by way of an e mail, suggesting that they could have been the goal of spyware and adware. “Apple detected that you’re being focused by a mercenary spyware and adware assault that’s making an attempt to remotely compromise the iPhone related together with your Apple ID -xxx-,” learn the e-mail, as detailed right here: Apple warns customers in 92 nations of spyware and adware assault.
It’s not all the time a flaw in Apple’s software program that may go away Macs weak. In August 2023 a critical vulnerability that affected Intel processors was highlighted. Affected gadgets included Intel-powered Macs from 2015 onwards (M-series Macs have been all okay). In accordance with researcher Daniel Moghimi: “Downfall assaults goal a crucial weak point present in billions of contemporary processors utilized in private and cloud computer systems.” Intel launched a patch, however it’s not the primary time this has occurred. Again in 2018, in an identical case, Meltdown and Spectre attacked vulnerabilities in Intel and ARM processors. That danger was mitigated by updates to the working system which closed off the areas that have been uncovered.
Such vulnerabilities, although uncommon, might enable an attacker root entry to your Mac.
What does Apple do about hacks
Apple has gone to nice lengths to make it tough for hackers to realize entry to Macs. With the protections provided by Gatekeeper, the Safe Enclave options of the M-series of chips, and the T1 or T2 chip in some Intel-powered Macs, plus Apple’s built-in antivirus XProtect, focusing on Macs might be thought of an excessive amount of effort by hackers. We focus on this in additional element right here: How safe is a Mac? and in Do Macs want antivirus software program?
Nonetheless, now and again safety vulnerabilities are detected that could possibly be utilized by hackers to use Macs. These vulnerabilities are generally known as again doorways or as a zero-day vulnerability. When these are recognized by safety researchers (or pleasant hackers) they often alert Apple to them within the hope that the corporate will rapidly shut the vulnerability, rapidly – or inside zero days – earlier than it’s exploited.
Apple encourages researchers to level out vulnerabilities, and when a vulnerability is found, Apple is often fast to repair. Apple has even paid cash to those that introduced safety flaws to its consideration. For instance, in 2021, Apple paid a pupil $100,000 after he found a harmful vulnerability regarding Macs and reported it to Apple. The vulnerability, which might allow a hacker to realize management of a Mac person’s digital camera, was recognized by Ryan Pickren in July 2021 and stuck by Apple in macOS Monterey 12.0.1 on October 25, 2021. Extra info right here: Hacker ‘might take over any Apple webcam’.
However there have been circumstances the place Apple has been criticized for being gradual to reply to the menace as soon as it’s been recognized. For instance, researcher Filippo Cavallarin discovered a Gatekeeper vulnerability in 2019 that he alerted Apple to. Having had no response from Apple inside 90 days he went public with particulars of the vulnerability.
How does Apple defend Macs from hackers
Apple is stored busy patching these safety flaws as and after they come up, however it was reliant on customers to put in them. Earlier than Apple launched macOS Ventura in 2022 an replace to the working system was required to get the vital safety element on a Mac. Since some individuals delay putting in working system updates this was problematic so Apple modified the way in which safety updates are utilized to Macs. These vital safety updates can now be delivered as background updates that may be routinely put in on a Mac with out the person having to do something – though we suggest you verify the next to make sure it’s arrange in your Mac:
- Open System Settings.
- Select Normal.
- Click on on the i beside Automated Updates.
- Ensure that the choice to Set up Safety Responses and system information is chosen, even if you happen to select to not choose the others (though we suggest you do).
Now your Mac will verify for updates, obtain the replace, and set up the replace with out you needing to do something.
In the event you aren’t working a latest model of macOS then Apple received’t be issuing any safety updates for you. Apple solely points safety updates for the present three variations of macOS, see: How lengthy does Apple help Macs for. For that motive we suggest that you’ve got a Mac that helps no less than the model of macOS from two years in the past. Currenly solely macOS Tahoe, which launched in fall 2025, macOS Sequoia and macOS Sonoma are supported with safety updates. Fortunately this does imply most Macs from 2018 and later are supported. Learn: The most recent model of macOS your Mac can run.
Can a Mac digital camera be hacked?
As soon as a hacker has entry to your Mac there are numerous methods during which they could attempt to acquire details about you or use the processing energy of your Mac for their very own functions. As we talked about above, within the case of spyware and adware the hacker would possibly try to put in a keylogger in order that it could possibly report what you’re typing and look out on your password. The hacker might additionally try to hijack your mic or video digital camera.
Theoretically, this shouldn’t be doable: since macOS Catalina launched in 2019 Apple has protected Mac customers from a majority of these exploits by making certain that you must give your permission earlier than the mic or video digital camera is used, or earlier than a display screen recording can happen. And in case your video digital camera is getting used you’ll all the time see a inexperienced mild subsequent to it. Nonetheless, the instance we talked about above, the place Ryan Pickren alerted Apple to a vulnerability that might allow a hacker to realize management of a Mac person’s digital camera, means that Apple’s alert wasn’t sufficient to cease the digital camera from being accessed.
There was additionally a camera-related vulnerability that affected Mac customers of the video conferencing service Zoom. On this case, hackers might add customers to video calls with out them understanding after which activate their webcams however preserve the sunshine turned off. This may allow any potential hackers (or legislation enforcement our bodies) to observe your actions and also you wouldn’t have any concept that the digital camera was watching you. Zoom patched the vulnerability, however solely after it turned public information when the one who discovered it reported that the flaw had been left in place for 3 months after the corporate had been privately knowledgeable of the chance. For extra info learn: Learn how to cease your Mac webcam being hacked.
Questioning about whether or not FaceTime is safe? Learn Is Apple FaceTime protected?

Dominik Tomaszewski / Foundry
Glossary of phrases
We’ll run by way of the forms of hacks which can be extra pertinent to the hacking of Macs under:
Cryptojacking: That is the place somebody makes use of your Mac’s processor and RAM to mine cryptocurrency. In case your Mac has slowed proper down this could possibly be the offender.
Spyware and adware: Right here hackers try to collect delicate information about you, akin to your log in particulars. They may use key loggers to report what you sort and finally have the data they should log in to your accounts. In a single instance, the OSX/OpinionSpy spyware and adware was stealing information from contaminated Macs and promoting it on the darkish internet.
Ransomware: Some criminals use Ransomware to try to extort cash from you. In circumstances like KeRanger hackers might have encrypted information on Macs after which demand cash to unencrypt them. Fortunately Safety researchers recognized KeRanger earlier than it began infecting Macs so it was addressed earlier than it turned a critical menace. In April 2023 safety researchers warned {that a} collective often known as LockBit was engaged on ransomware encryptors that work on each Macs utilizing Apple M-series chips and Intel processors.
Botnet: On this case, your pc turns into a remotely operated spam machine. Within the case of the Trojan Horse botnet OSX.FlashBack over 600,000 Mac computer systems.
Proof-of-concept: Typically the menace isn’t truly seen within the wild, however is a proof of idea primarily based on a loophole or vulnerability in Apple’s code. Whereas that is much less of a menace the priority is that if Apple isn’t fast sufficient to shut the vulnerability it could possibly be utilized by criminals. In a single instance Google’s Mission Zero group designed a proof-of-concept often known as Buggy Cos which was capable of acquire entry to elements of macOS because of a bug in macOS’ reminiscence supervisor.
Port exploits: It’s not all the time the case that the hack is made doable by some type of malware downloaded onto the Mac. In some circumstances, Macs have been hacked after one thing is plugged right into a port. It’s doable that Macs could possibly be hacked by way of the USB and by the Thunderbolt port – which is an effective motive to all the time watch out about what you plug into your Mac or go away your Mac unattended. For instance, within the checkm8 exploit it might have been doable for hackers to realize entry to the T2 chip by plugging in a modified USB-C cable. Equally, within the case of Thunderspy a critical vulnerability with the Thunderbolt port might have granted a hacker entry to a Mac.
Feeling safer now? Be taught much more by studying the useful ideas in Learn how to preserve your Mac safe.

