
A brand new Android malware-as-a-service (MaaS) named Cellik is being marketed on underground cybercrime boards providing a sturdy set of capabilities that embrace the choice to embed it in any app obtainable on the Google Play Retailer.
Particularly, attackers can choose apps from Android’s official app retailer and create trojanized variations that seem reliable and maintain the actual app’s interface and performance.
By offering the anticipated capabilities, Cellik infections can go unnoticed for an extended time. Moreover, the vendor claims that bundling the malware this fashion could assist bypass Play Shield, though that is unconfirmed.
Cell safety agency iVerify found Cellik on underground boards the place it’s provided for $150/month or $900 for lifetime entry.
Cellik capabilities
Cellik is a fully-fledged Android malware that may seize and stream the sufferer’s display in actual time, intercept app notifications, browse the filesystem, exfiltrate recordsdata, wipe knowledge, and talk with the command-and-control server by way of an encrypted channel.
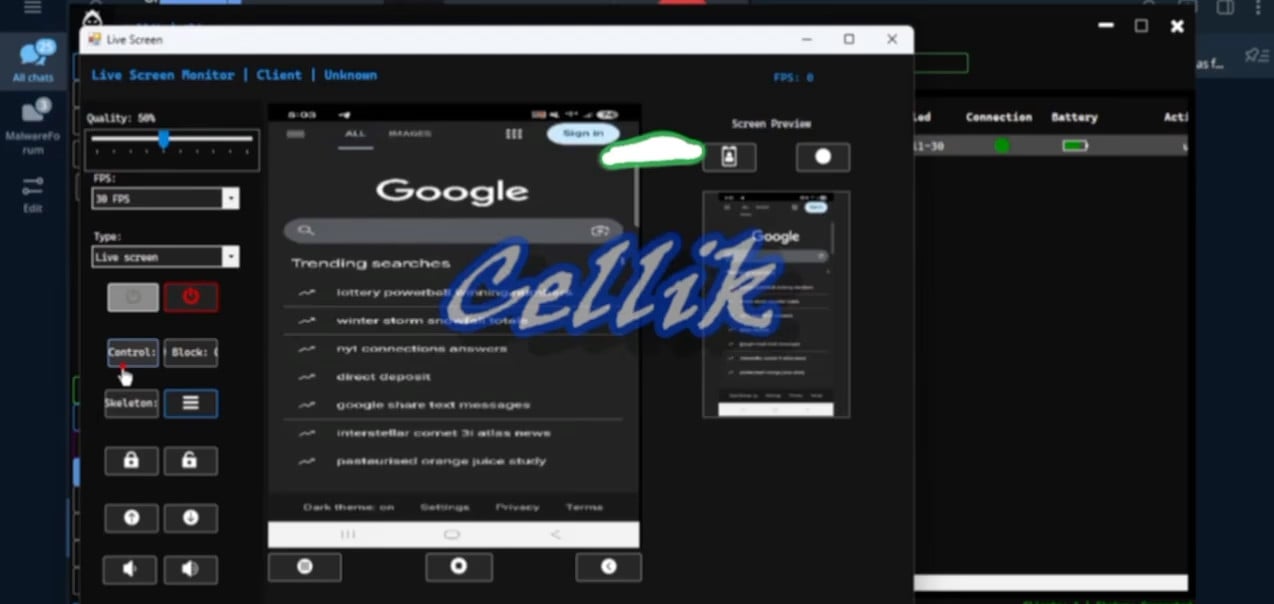
Supply: iVerify
The malware additionally encompasses a hidden browser mode that attackers can use to entry web sites from the contaminated machine utilizing the sufferer’s saved cookies.
An app injection system permits attackers to overlay faux login screens or inject malicious code into any app to steal the sufferer’s account credentials.
The listed capabilities additionally embrace the choice to inject payloads onto put in apps, which might make pinpointing the an infection much more tough, as long-trusted apps abruptly flip rogue.

Supply: iVerify
The spotlight, although, is the Play Retailer integration into Cellik’s APK builder, which permits cybercriminals to browse the shop for apps, choose those they need, and create a malicious variant of them.
“The vendor claims Cellik can bypass Google Play safety features by wrapping its payload in trusted apps, basically disabling Play Shield detection,” explains iVerify.
“Whereas Google Play Shield sometimes flags unknown or malicious apps, trojans hidden inside standard app packages would possibly slip previous automated opinions or device-level scanners.”
BleepingComputer has contacted Google to ask if Cellik-bundled apps can certainly evade Play Shield, however a remark wasn’t instantly obtainable.
To remain protected, Android customers ought to keep away from sideloading APKs from doubtful websites until they belief the writer, guarantee Play Shield is energetic on the machine, overview app permissions, and monitor for uncommon exercise.
Damaged IAM is not simply an IT drawback – the affect ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM appears to be like like, and a easy guidelines for constructing a scalable technique.



