
iCloud Calendar invitations are being abused to ship callback phishing emails disguised as buy notifications immediately from Apple’s e-mail servers, making them extra prone to bypass spam filters to land in targets’ inboxes.
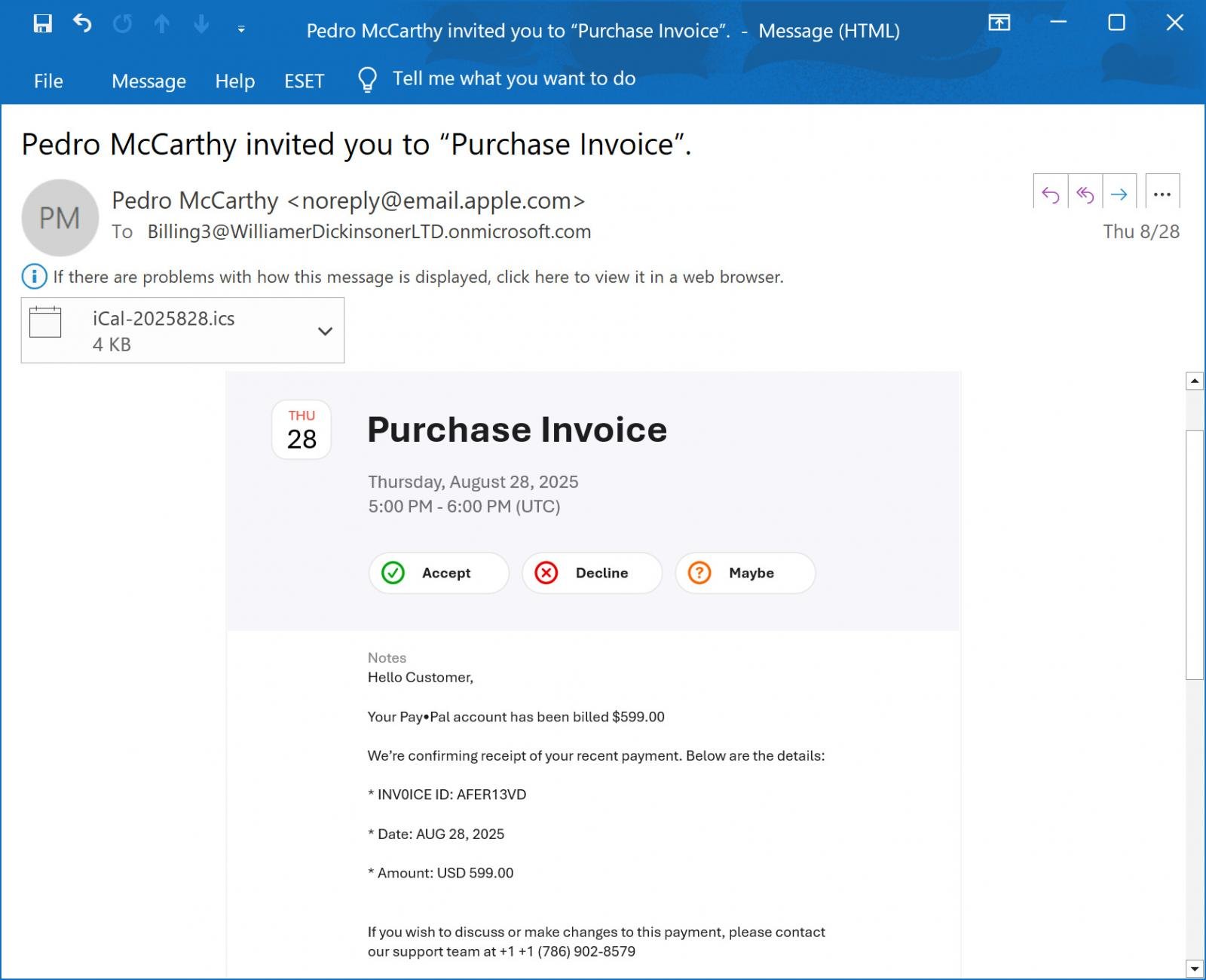
Earlier this month, a reader shared an e-mail with BleepingComputer that claimed to be a cost receipt for $599 charged towards the recipient’s PayPal account. This e-mail included a telephone quantity if the recipient needed to debate the cost or make adjustments to it.
“Good day Buyer, Your PayPal account has been billed $599.00. We’re confirming receipt of your current cost,” learn the e-mail.
“When you want to talk about or make adjustments to this cost, please contact our help workforce at +1 +1 (786) 902-8579. Contact us to cancel +1 (786) 902-8579,” continued the e-mail.
Supply: BleepingComputer
The purpose of those emails is to trick recipients into considering their PayPal account was fraudulently charged to make a purchase order and scare the e-mail recipient into calling the scammer’s “help” telephone quantity.
When calling the quantity, a scammer will attempt to scare you into considering your account was hacked or that they want to hook up with your pc to provoke a refund, asking you to obtain and run software program.
Nevertheless, in earlier scams like this, this distant entry was used to steal cash from financial institution accounts, deploy malware, or steal information from the pc.
Abusing iCloud Calendar invitations to ship emails
The lure on this e-mail is a typical callback phishing rip-off, however what was unusual was that it was despatched from noreply@e-mail.apple.com, passing the SPF, DMARC, and DKIM e-mail safety checks, signifying that it legitimately got here from Apple’s mail server.
Authentication-Outcomes: spf=cross (sender IP is 17.23.6.69)
smtp.mailfrom=e-mail.apple.com; dkim=cross (signature was verified)
header.d=e-mail.apple.com;dmarc=cross motion=none header.from=e-mail.apple.com;
As you’ll be able to see from the above phishing e-mail, this e-mail is definitely an iCloud Calendar invite, the place the menace actor included the phishing textual content throughout the Notes area after which invited a Microsoft 365 e-mail deal with that they managed.
When the iCloud Calendar occasion is created and exterior individuals are invited, an e-mail invitation is distributed from Apple’s servers at e-mail.apple.com from the iCloud Calendar proprietor’s title with the e-mail deal with “noreply@e-mail.apple.com”
Within the e-mail seen by BleepingComputer, the invitation is addressed to a Microsoft 365 account, “Billing3@WilliamerDickinsonerLTD.onmicrosoft.com”.
Much like a earlier phishing marketing campaign that utilized PayPal’s “New Deal with” function, it’s believed that the Microsoft 365 e-mail deal with to which the invite is distributed is definitely a mailing listing that robotically forwards any e-mail it receives to all different group members.
On this case, the mailing listing members are the targets of the phishing rip-off.
As the e-mail was initially initiated from Apple’s e-mail servers, whether it is forwarded by Microsoft 365, it will often fail SPF e-mail checks.
To stop this, Microsoft 365 makes use of the Sender Rewriting Scheme (SRS) to rewrite the Return path to an deal with related to Microsoft, permitting it to cross SPF checks.
Unique Return-Path: noreply@e-mail.apple.com
Rewritten Return-Path: bounces+SRS=8a6ka=3I@williamerdickinsonerltd.onmicrosoft.com
Whereas there may be nothing notably particular concerning the phishing lure itself, the abuse of the reputable iCloud Calendar invite function, Apple’s e-mail servers, and an Apple e-mail deal with provides a way of legitimacy to the e-mail and likewise permits it to doubtlessly bypass spam filters because it comes from a trusted supply.
As a normal rule, in case you obtain an surprising Calendar invite with an odd message inside it, it must be handled with warning.
BleepingComputer contacted Apple about this rip-off, however didn’t obtain a response to our e-mail.


