
A brand new GlassWorm malware assault by way of compromised OpenVSX extensions focuses on stealing passwords, crypto-wallet knowledge, and developer credentials and configurations from macOS programs.
The risk actor gained entry to the account of a respectable developer (oorzc) and pushed malicious updates with the GlassWorm payload to 4 extensions that had been downloaded 22,000 instances.
GlassWorm assaults first appeared in late October, hiding the malicious code utilizing “invisible” Unicode characters to steal cryptocurrency pockets and developer account particulars. The malware additionally helps VNC-based distant entry and SOCKS proxying.
Over time and throughout a number of assault waves, GlassWorm impacted each Microsoft’s official Visible Studio Code market and its open-source various for unsupported IDEs, OpenVSX.
In a earlier marketing campaign, GlassWorm confirmed indicators of evolution, focusing on macOS programs, and its builders have been working so as to add a substitute mechanism for the Trezor and Ledger apps.
A new report from Socket’s safety staff describes a brand new marketing campaign that relied on trojanizing the next extensions:
- oorzc.ssh-tools v0.5.1
- oorzc.i18n-tools-plus v1.6.8
- oorzc.mind-map v1.0.61
- oorzc.scss-to-css-compile v1.3.4
The malicious updates have been pushed on January 30, and Socket studies that the extensions had been innocuous for 2 years. This implies that the oorzc account was most probably compromised by GlassWorm operators.
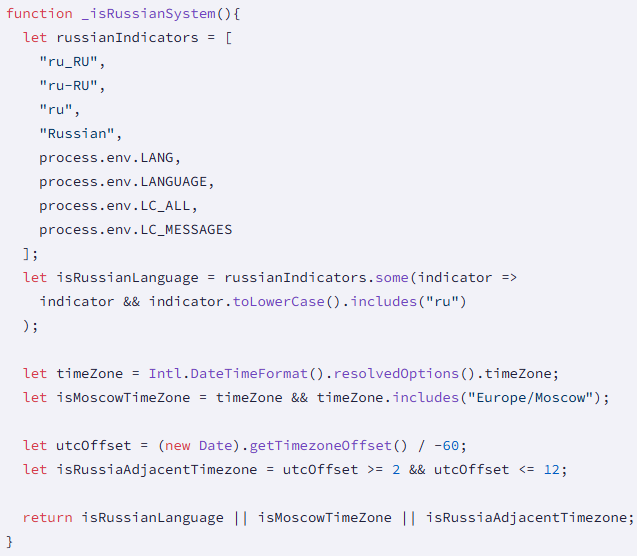
Based on the researchers, the marketing campaign targets macOS programs completely, pulling directions from Solana transaction memos. Notably, Russian-locale programs are excluded, which can trace on the origin of the attacker.
Supply: Socket
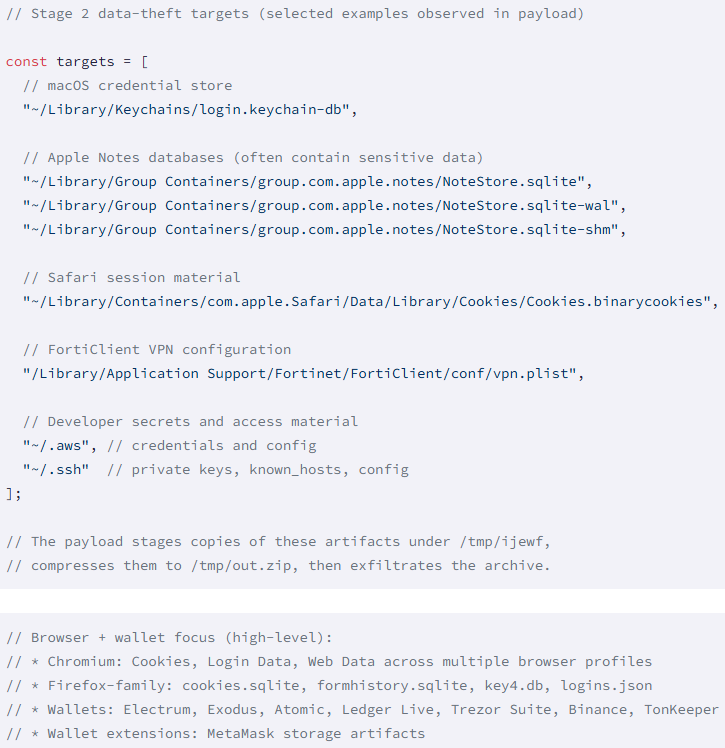
GlassWorm hundreds a macOS data stealer that establishes persistence on contaminated programs by way of a LaunchAgent, enabling execution at login.
It harvests browser knowledge throughout Firefox and Chromium, pockets extensions and pockets apps, macOS keychain knowledge, Apple Notes databases, Safari cookies, developer secrets and techniques, and paperwork from the native filesystem, and exfiltrates every thing to the attacker’s infrastructure at 45.32.150[.]251.
Supply: Socket
Socket reported the packages to the Eclipse Basis, the operator of the Open VSX platform, and the safety staff confirmed unauthorized publishing entry, revoked tokens, and eliminated the malicious releases.
The one exception is oorzc.ssh-tools, which was eliminated utterly from Open VSX as a result of discovering a number of malicious releases.
At present, variations of the affected extensions available on the market are clear, however builders who downloaded the malicious releases ought to carry out a full system clean-up and rotate all their secrets and techniques and passwords.



